In today’s interconnected digital landscape, safeguarding your valuable data and network infrastructure is paramount. Cloud firewalls offer a robust and scalable solution to protect your cloud resources from unauthorized access and malicious attacks. Understanding how cloud firewalls work and their crucial role in modern security postures is essential for any organization utilizing cloud services. This article delves into the intricacies of cloud firewalls, exploring their functionality, benefits, and the reasons why implementing one is a non-negotiable aspect of a comprehensive security strategy in the cloud. Whether you are running applications in a public, private, or hybrid cloud environment, the information presented here will equip you with the knowledge to make informed decisions about protecting your critical assets.
Cloud firewalls act as a vital security barrier between your cloud environment and the outside world, inspecting and filtering network traffic based on pre-defined rules. They provide advanced threat protection against a wide array of cyber threats, including malware, intrusion attempts, and denial-of-service attacks. By deploying a cloud firewall, businesses can significantly reduce their security risks, enhance compliance with industry regulations, and ensure business continuity in the face of evolving cyber threats. This article will explore the different types of cloud firewalls available, their deployment models, and key features to consider when selecting the right solution for your specific needs. Learn how cloud firewall solutions can strengthen your overall security posture and help you maintain a secure cloud environment.
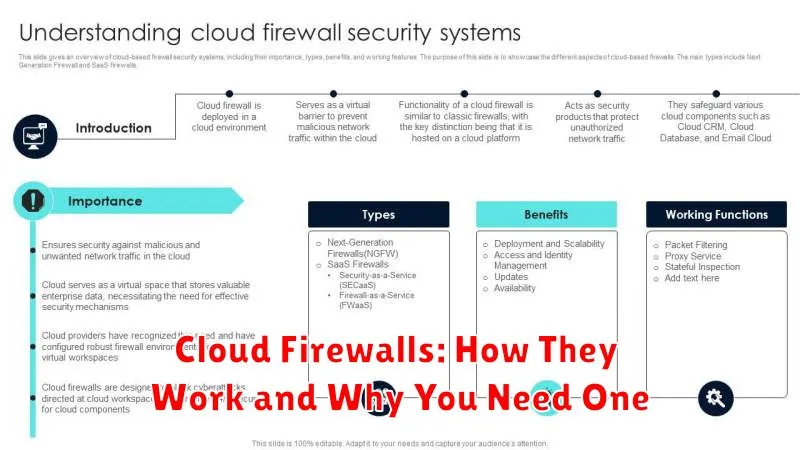
What Is a Cloud Firewall?
A cloud firewall is a network security service that protects your cloud infrastructure by filtering traffic to and from your cloud resources. It operates in the cloud, rather than on premises, and enforces security policies to prevent unauthorized access and malicious activity.
Think of it as a gatekeeper for your cloud environment. Just like a traditional firewall protects your local network, a cloud firewall safeguards your virtual networks, applications, and data residing in the cloud. It inspects incoming and outgoing network traffic and blocks any traffic that doesn’t meet your predefined security rules.
Cloud firewalls offer several key benefits including scalability, flexibility, and cost-effectiveness. They can easily adapt to changing network demands, offering centralized management across multiple cloud platforms. This eliminates the need for physical hardware and reduces administrative overhead.
Several types of cloud firewalls exist, including: Next-Generation Firewalls (NGFWs) that provide advanced threat protection, Web Application Firewalls (WAFs) that protect web applications from attacks, and Distributed Denial of Service (DDoS) protection services that mitigate DDoS attacks.
Types: Network-Based vs Host-Based
Cloud firewalls can be broadly categorized into two main types: network-based and host-based. Network-based firewalls filter traffic at the network perimeter, examining packets as they enter or leave the network. They act as a first line of defense, protecting multiple systems behind them. These firewalls are typically deployed as virtual appliances or integrated services within a cloud provider’s infrastructure.
Host-based firewalls, on the other hand, are installed and operate directly on individual cloud instances or virtual machines. They provide a granular level of control over traffic entering and leaving the specific host. Host-based firewalls are essential for defense-in-depth, adding another layer of security even if the network perimeter is breached. They are often configured through software applications or operating system settings.
Choosing the right type depends on the specific security needs and architecture of your cloud environment. Many organizations employ a combination of both network-based and host-based firewalls for comprehensive protection.
Setting Up Rules and Access Controls
A crucial aspect of cloud firewall management involves configuring rules and access controls. These rules dictate which traffic is permitted or denied based on specific criteria. Source and destination IP addresses, ports, and protocols are commonly used parameters.
Rules can be established based on pre-defined security policies or customized to meet specific organizational needs. For instance, a rule might allow inbound HTTP traffic on port 80 while blocking all other incoming connections. Another rule could permit outbound traffic to a specific IP range while denying connections to all others. The order of rules is important, as the firewall processes them sequentially.
Access controls further refine security by granting or restricting access based on user identities, roles, or groups. Integrating with identity and access management (IAM) systems enables granular control over who can access specific resources and perform certain actions.
Many cloud firewalls offer a visual interface for rule creation and management, simplifying the process. Some platforms also support scripting and automation for more complex configurations.
Integration with Cloud Providers
Cloud firewalls are designed to integrate seamlessly with various cloud platforms. This tight integration allows for centralized management and automated provisioning of security policies across different cloud environments. Compatibility with major cloud providers like AWS, Azure, and Google Cloud is crucial for organizations operating in multi-cloud or hybrid cloud architectures.
Integration benefits include simplified deployment and orchestration. Automated deployments reduce manual configuration, minimizing human error and speeding up the implementation process. Orchestration capabilities enable dynamic scaling and adaptation of firewall policies in response to changing workloads and traffic patterns.
Native integration leverages the cloud provider’s existing infrastructure and services for enhanced performance and security. This often allows for deeper visibility into network traffic and more granular control over security policies. For example, integration might allow the firewall to directly interact with identity and access management (IAM) services for more context-aware access control.
Logging and Monitoring Traffic
Logging and monitoring are crucial aspects of cloud firewall management. Cloud firewalls meticulously log traffic flowing through them, providing valuable insights into network activity. These logs capture essential information such as source and destination IP addresses, ports, timestamps, and the action taken by the firewall (allow or deny).
This data allows administrators to identify trends, detect anomalies, and investigate security incidents. For example, a sudden surge in traffic from a specific region might indicate a distributed denial-of-service (DDoS) attack. Similarly, attempts to access blocked ports could signal malicious activity.
Monitoring tools provide real-time visibility into traffic patterns and firewall performance. They often include dashboards and visualizations that make it easy to identify potential problems. Automated alerts can notify administrators of suspicious activity or performance degradations, enabling rapid response and mitigation.
Retention policies are essential for managing log data. Defining appropriate retention periods ensures compliance requirements are met and provides sufficient historical data for analysis.
Firewall Best Practices in 2025
Implementing a firewall is just the first step. Maintaining its effectiveness requires adherence to best practices. In 2025, with the evolving threat landscape, these practices are more critical than ever. Regular audits are essential to ensure the firewall configuration aligns with current security policies and organizational needs.
Principle of least privilege should be the foundation of all firewall rules. Grant only necessary access and restrict everything else. This minimizes the potential impact of a breach. Microsegmentation takes this further by dividing the network into smaller, isolated segments, limiting the lateral movement of attackers.
Automated threat intelligence feeds are vital for staying ahead of emerging threats. These feeds dynamically update firewall rules to block known malicious traffic and patterns. Regularly updating firmware is crucial for patching vulnerabilities and ensuring optimal performance. Multi-factor authentication (MFA) for firewall management access adds an extra layer of security, preventing unauthorized changes.
Finally, comprehensive logging and monitoring provides visibility into network traffic and allows for rapid incident response. Analyzing logs can reveal potential threats and inform future security enhancements.
Common Mistakes to Avoid

Implementing a cloud firewall effectively requires a proactive approach and awareness of common pitfalls. One frequent mistake is overly permissive rules. Granting excessive access can leave your cloud resources vulnerable. Start with a deny-all approach and only open necessary ports and protocols.
Another common error is neglecting regular rule reviews. Cloud environments are dynamic. Outdated rules may no longer be relevant or may even introduce security gaps. Regular audits and updates are essential.
Lack of visibility is another significant issue. Without proper monitoring and logging, identifying malicious activity or troubleshooting connectivity problems becomes difficult. Implement comprehensive logging and utilize monitoring tools to gain insights into traffic patterns.
Finally, inadequate training can undermine your cloud firewall’s effectiveness. Ensure your team understands how to configure, manage, and monitor the firewall properly. Regular training and updates on best practices are critical.